The Crucial Role of Port Scanners in Network Security Port scanners are essential tools in the field of network security. They help identify vulnerabilities within systems by scanning for open ports. Each open port can be a potential entry point for hackers. By using port scanners, organizations can gather information about their network’s security posture. This proactive approach aids in defending against cyber threats.
Understanding the Need for Port Scanning: Vulnerability Assessment Every network has many ports that software applications use to communicate. Not all of these ports are secure. Port scanning helps identify which ports are open and which services are running. This information is vital for detecting weaknesses that attackers could exploit. Regularly assessing vulnerabilities through port scanning is a key part of maintaining network security.
A Brief Overview of Port Scanning Techniques Various techniques exist for port scanning. Understanding these methods is crucial for effective security assessments:
- TCP Connect Scan: This straightforward method connects to each port to check if it is open.
- TCP SYN Scan: This stealthier approach sends a SYN packet but doesn’t complete the handshake.
- UDP Scan: Unlike TCP, UDP scans verify the status of UDP ports, often revealing different vulnerabilities.
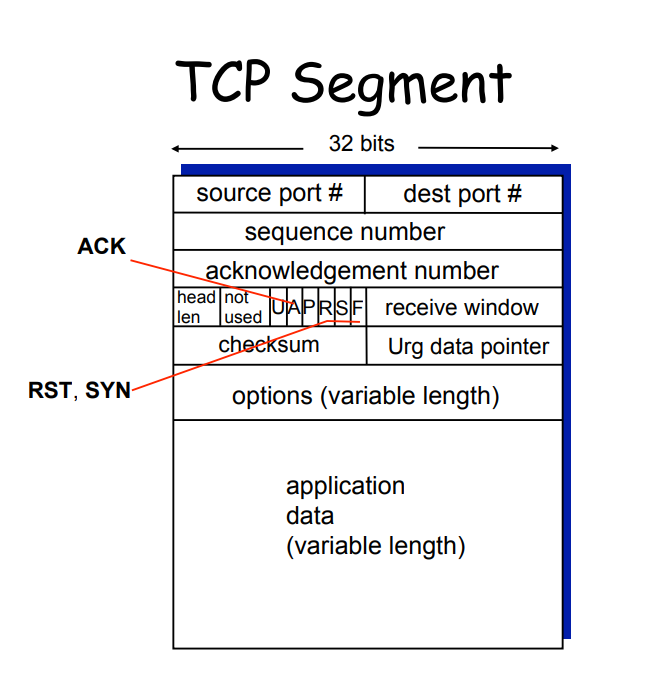
Understanding IP Addresses and Ports
IP Addresses: The Foundation of Network Communication
An IP address is like a home address for devices on a network. Each device needs a unique IP to communicate. This unique identifier allows information to be routed correctly.
TCP/UDP Ports: The Gateways to Applications
Ports act as gateways for applications. They enable specific communication channels for different services. Here’s how they bifurcate:
- TCP Ports: Ensure reliable communication and are used by protocols like HTTP and FTP.
- UDP Ports: Allow faster, connectionless communication, often used for streaming and gaming.
Port Numbers and Their Significance
Ports are numbered from 0 to 65535. Each number has a specific purpose. Some ports are well-known, like:
- Port 80: Commonly used for HTTP traffic.
- Port 443: Used for HTTPS, securing web traffic.

Common Port Scanning Techniques
TCP Connect Scan: A Basic Approach
The TCP connect scan is the simplest method. It attempts to establish a full connection to each target port. If the connection succeeds, the port is open.
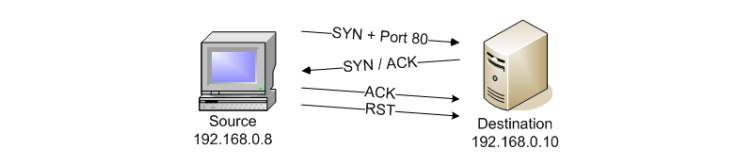
TCP SYN Scan: Stealthier and More Efficient
This method is stealthier than the TCP connect scan. It only sends a SYN packet and waits for a response, reducing detection chances. If a SYN-ACK response is received, the port is open.
UDP Scan: Exploring UDP-Based Services
UDP scanning can be challenging yet essential. Since UDP is connectionless, identifying open ports often involves sending specific packets and analyzing responses, if any.
Analyzing Scan Results: Identifying Vulnerabilities
Interpreting Scan Output: Identifying Open Ports
Upon completing a scan, you’ll get a list of open ports. This list reveals potential vulnerabilities. Interpreting this data correctly is essential for following up on security measures.
Common Vulnerabilities Associated with Open Ports
Open ports often correlate with vulnerabilities. Common issues include:
- Outdated Software: Older versions might have known bugs.
- Misconfigurations: Improper setups can expose sensitive information.
Prioritizing Vulnerabilities Based on Severity
Not all vulnerabilities pose equal risks. Prioritize based on:
- Exploitability: How easy is it for an attacker to exploit the vulnerability?
- Impact: What would happen if the vulnerability were exploited?
Tools and Technologies for Port Scanning
Nmap: A Widely Used and Powerful Port Scanner
Nmap is one of the most popular tools for port scanning. It offers robust features, allowing users to perform a variety of scans while providing detailed analysis.
Nessus: Integrating Port Scanning with Vulnerability Management
Nessus combines port scanning with vulnerability management. It provides insights into how to fix the vulnerabilities identified during the scan.
Other Notable Port Scanning Tools
- Zenmap: A user-friendly interface for Nmap.
- Masscan: An exceptionally fast scanner for large networks.
- OpenVAS: A full-fledged vulnerability scanner.
Ethical Considerations and Legal Implications
Responsible Use of Port Scanners: Avoiding Legal Issues
Using port scanners comes with ethical responsibilities. Scanning without consent can lead to serious legal repercussions. It is vital to ensure permission before initiating scans.
Obtaining Permission Before Scanning: Best Practices
Always obtain written permission from the network owner. This helps avoid misunderstandings and provides a clear framework for scanning activities.
The Importance of Ethical Hacking Principles
Embracing ethical hacking principles ensures that security practices remain legal and responsible. Ethical hackers focus on protecting systems rather than exploiting them.
Why Port Scanners Are Used: Legitimate and Malicious Purposes
Network Security Audits
Organizations use port scanners to perform security audits and vulnerability assessments. This helps identify weaknesses in their networks.
Configuration and Maintenance
Scanning can confirm if open ports are set correctly for application configurations.
Malicious Activities
Unfortunately, port scanners can also be used for reconnaissance in cyberattacks. Hackers probe networks to find weaknesses to exploit.
Real-World Example In 2017, the Equifax breach demonstrated how a simple vulnerability scan led to a massive data breach, affecting millions of individuals.
Protecting Your Systems from Port Scans
Firewalls and IDS

Using firewalls and Intrusion Detection Systems (IDS) can help filter unwanted traffic. These tools can block or alert you about suspicious scanning activities.
Regular Updates
Keeping software up to date is essential. Regular patches can close vulnerabilities that scans might find.
Best Practices
- Secure all devices connected to your network.
- Regularly monitor network traffic.
- Use strong, unique passwords for devices.
Network Segmentation
Dividing your network into segments can limit the impact of a potential breach, making it harder for attackers to move laterally.
Conclusion: Securing Your Digital Assets in the Age of Network Scanning Understanding how port scanners function is vital in today’s digital environment. They play a significant role in both cybersecurity and attacks.
Key Takeaways:
- Port scanning reveals open ports and services.
- Tools like Nmap and Nessus can help assess vulnerabilities.
- Ethical guidelines exist to govern the use of port scanners.
Stay informed. Engage in learning more about network security. Proactive measures can protect digital assets and secure your information.
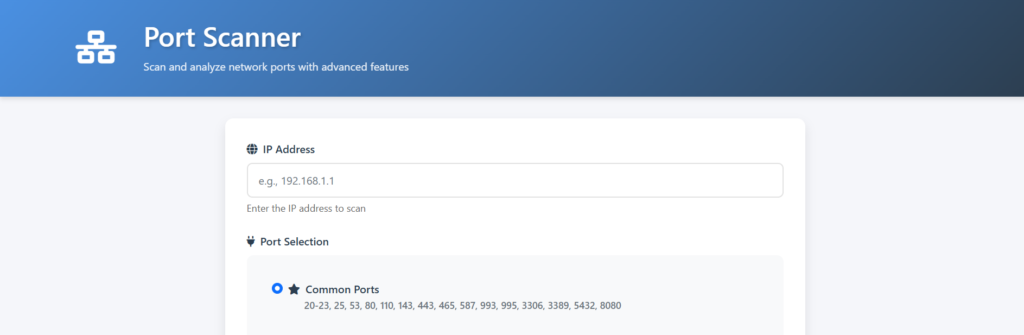
To explain this topic more clearly, you can make it easier to understand by using the Port Scanner tool I developed in Go. Here is the link: https://github.com/yusufdalbudak/advanced-port-scanner. Let’s try this out as I integrate it into my program.
1. I’m running the program locally via VSCode:
2. I access the program running on my local machine:
3. I enter the IP address I want to scan and usually prefer to scan for commonly open ports:
4. I start the scan by clicking the ‘Start Scan’ button:
5. I can view the open ports through the results displayed:
REFERENCES
- 1. Nmap Official Website: Nmap.org. Nmap. https://nmap.org/
- 2. Tenable Nessus: Tenable, Inc. Nessus. https://www.tenable.com/products/nessus
- 3. Network and Port Scanning: Shen, C.-C. Network and port scanning. University of Delaware. Email: cshen@cis.udel.edu
- 4. Port Scanning Utility: Khandelwal, S., Awasthi, A., & Chintan, V. Port scanning utility (Group 15). Indian Institute of Technology Kanpur. Emails: sourav@iitk.ac.in, anuraga@iitk.ac.in, vismay@iitk.ac.in
- 5. Port Scanning Techniques Tools and Detection: Coyle, S. Port scanning techniques, tools, and detection. Preprints. https://doi.org/10.20944/preprints202403.0225.v1
- 6. A Review of Port Scanning Techniques: de Vivo, M., Carrasco, E., Isern, G., & de Vivo, G. O. A review of port scanning techniques. Caracas, Venezuela. Emails: mdevivo@reacciun.ve, ecarrasco@ciens.ucv.ve, gisern@ciens.ucv.ve, gdevivo@reacciun.ve

Comments are closed